



Next: Configuration
Up: Security
Previous: Policy
Contents
Users should be aware that they are exposed to risks outside the firewall.
The log messages from syslog must be monitored frequently.
Restricted executions should always be applied and only enable file send and retrieval if it is absolutely necessary.
Actimd should be started as another used id and preferably without home directory.
Otherwise outsiders can search through users' home directories, especially the .actimrc file.
For example, the actim rpm package creates a new user, actim, and should run actimd as:
[joe@pebbles]$ su -c 'actimd -c /tmp/.actimdrc.joe' actim.
Then users can request the server to poll for actim emails:
[joe@pebbles]$ actim -C POLL EMAIL SETUP_USER
Suppose a restricted execution is setup as 'ls -l 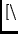 w/
w/![$]$](img15.png) *$'.
If an outsider tries to do 'ls -l /home/joe', then it will fail even though it satisfies the regular expression.
The risk of restricted commands is depends purely on how strict the regular expression is.
Alternatively, just make them as complete commands.
*$'.
If an outsider tries to do 'ls -l /home/joe', then it will fail even though it satisfies the regular expression.
The risk of restricted commands is depends purely on how strict the regular expression is.
Alternatively, just make them as complete commands.
Joseph Kuan
2001-10-16